Cyber security seems to be in the news on a weekly basis, from breaches, to identity theft, to massive settlements from companies who have misused or mishandled customer data. Cyber security is certainly a hot topic, and for good reason: In 2017, 54% of companies experienced one or more successful attack that compromised their data and/or IT infrastructure.1
Anyone who handles sensitive data is living in an increasingly dangerous world. This is all the more true for medical practitioners, for whom extensive compliance, regulation, and penalties for mishandling sensitive patient information have never been greater. According to Reuters, patient records can be 10 to 20 times more valuable than credit card information, so there is an obvious incentive for cybercriminals to target medical practices. After all, credit card numbers can be changed overnight, but addresses, employers, insurance documents, and diseases cannot.
What practical steps can ophthalmologists take to secure their practice in the age of daily attacks and extensive regulatory compliance? This article explores how to increase cyber security and mitigate risks associated with running a modern ophthalmic practice.

IN YOUR OFFICE
The no-brainer: antivirus software. Whenever you have multiple computers connected to the Internet (and each other) in a business environment, antivirus software is a must. Many ophthalmic practices run on Windows PCs, which means they’re particularly vulnerable. There are hundreds of thousands of known viruses for Windows, with more surfacing every day. For practices running a Macintosh environment, good antivirus software is still important. Software that can recognize threats, malicious files, and the like is incredibly important and an obvious first step in securing your practice.
Separate Wi-Fi networks. Another recommended measure is creating separate Wi-Fi networks for staff and for patients. This is a must when dealing with sensitive health information. Separating your Wi-Fi networks (or not offering in-office Wi-Fi to patients at all) is especially important if any of your diagnostic tools connect to the internet. The most recent numbers estimate that one out of four medical devices is connected to a network, so this is a huge potential liability.
Remember the 2013 Target breach, in which more than 40 million customer credit cards were compromised? The hackers (believed to be led by a 22-year-old Ukrainian) didn’t actually target Target itself; instead, they were able to breach the security of the HVAC contractor Target had hired to work on its systems. The HVAC vendor in question had access to the same Wi-Fi system that Target’s point-of-sale machines were on, so when they got hacked, Target’s entire system was compromised as well, and the hackers were able to obtain millions of customer records in just a few days.
VPN. Beyond separating public and private Wi-Fi networks, it also recommended that each computer in your physical office obtain and use a virtual private network (VPN) for further securing network communications. Have you ever used the public Wi-Fi in your local Starbucks to send an email or access your online banking? Unless you were using a VPN to encrypt your data, anyone else on that Wi-Fi network could theoretically see the information your device is sending and receiving. Say goodbye to that online banking password.
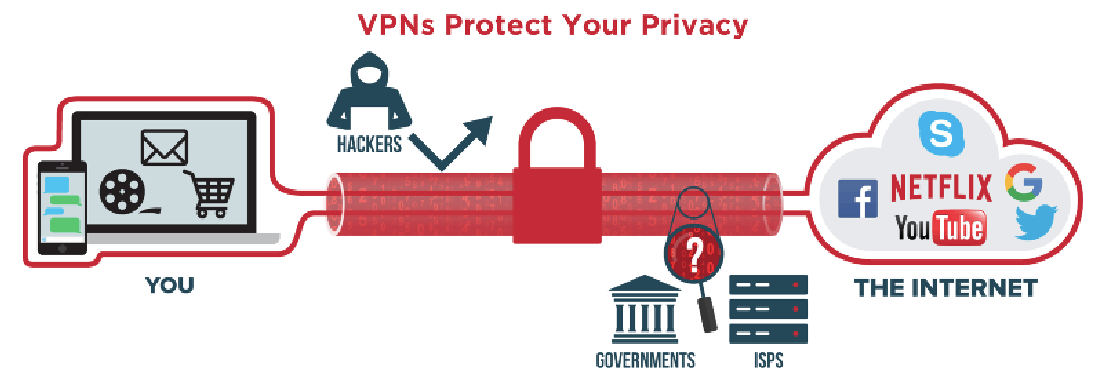
Figure 1 | VPNs encrypt data, making it useless and unreadable to anyone sniffing traffic on your network
A VPN stops others from being able to “sniff” your network traffic. Think of it as a tunnel—data is passing through, but it’s obscured to anyone trying to look in from the outside. Even if someone were to crack the Wi-Fi password for your main network, they wouldn’t be able to see any information coming through that network. VPNs take all data and encrypt it, making it useless and unreadable to anyone sniffing traffic on your network (Figure 1).
Figure 2 | Password management software can reset passwords to safer alphanumeric strings.
Password managers. So, you’ve separated your public Wi-Fi and the private network your office staff uses for billing, electronic health records, and diagnostic devices. But what if your office is broken into or physically compromised? One of the most practical security measures the average person can take is to strengthen his or her passwords. Password management software (eg, password.com/) is an incredibly easy way to store all of the passwords you use and reset your current passwords to random, virtually uncrackable alphanumeric strings (Figure 2). A shared team account is an easy way for office staff to share passwords for your practice’s most frequently used online services, from your website to social media accounts, billing applications, and more. You can delegate access to everyone in your organization or create separate “vaults” for different teams, giving access to only those who truly need it.
For reference, I tested the password I used to log onto my email this morning. It would take a supercomputer about 640 quintillion years to crack. In contrast, it would take only 19 minutes to crack the average American’s password. Perhaps it’s time to shred the sticky notes littering your office and trade them in for a more secure solution.
ON THE WEB
SSL. If you are serious about securing your practice from data breaches, you also need to consider the security of your website. Although implementation of website security measures can easily escalate to complex solutions, the easiest way to cover your bases is to install a Secure Sockets Layer (SSL) certificate on your website. SSL certificates encrypt all data sent to and from a website. Even if someone were able to intercept any data sent to or from your website (eg, appointment requests with sensitive patient information), the data would be unreadable. Most SSL certificates cost less than $100 per year, so, if you collect any sort of personal or health-related information on your website, this step is a no-brainer.
CDN. When handling sensitive patient information, security is the number one goal. But what about business goals? What if your website is attacked or goes down unexpectedly? What would the downtime cost your practice in terms of efficiency and revenue?

Using a content distribution network (CDN) such as Cloudflare can help mitigate this risk. Cloudflare has servers and data centers around the world that can increase uptime for your website and help handle the load, should your website receive lots of traffic or fall prey to a distributed denial-of-service (DDoS) attack. Cloudflare’s servers can also help serve your content to users faster and make your website safer and more secure, minimizing the potential for loss due to downtime or attacks.
Two-factor authentication. If there is one security technology that has been on the rise in recent years, it is two-factor authentication (2FA). 2FA is a verification process by which online services require not only a password but also something that you have physical access to, such as your cell phone. Have you ever tried to log into Facebook and been prompted for a six-digit passcode that was texted to your cell phone? That’s 2FA at work, and it’s much more secure than a traditional password alone.
Combined with a good password manager, 2FA is a powerful way to secure your online accounts and prevent unwanted intrusions. For example, my Facebook password is D7YCs$jmiahFqpnkGtLiGxvzR. Go ahead, try to log in. Because I have 2FA turned on, you won’t be able to log into my account unless you have physical access to my cell phone (which, last time I checked, was in my pocket). The website https://twofactorauth.org/ is a great resource for finding online services that support 2FA. I strongly recommend that you comb through the list and turn on 2FA for each account that you use, both personally and for your practice.
IN YOUR COMMUNICATIONS
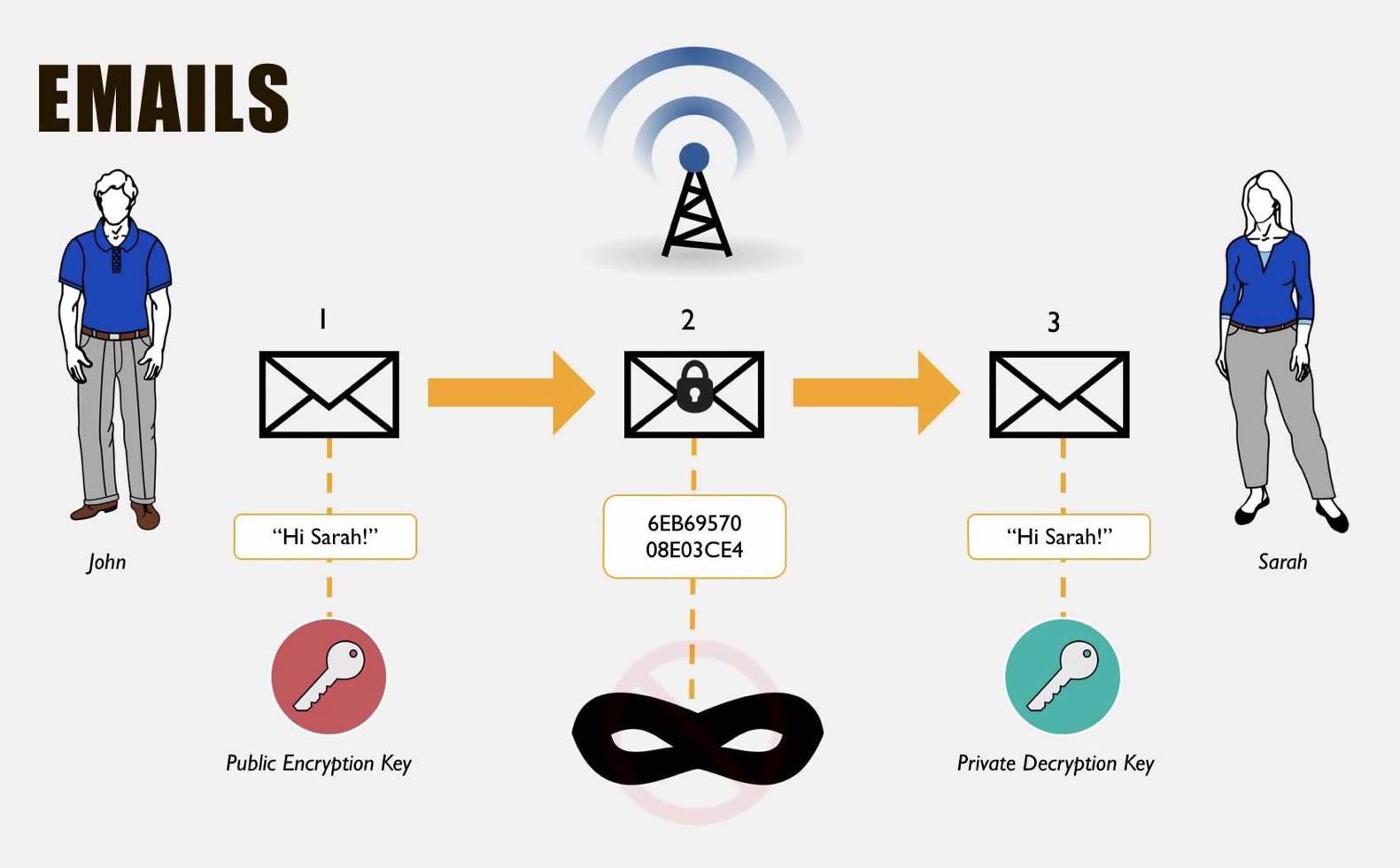
Encrypted email. What about your email communications? How can you ensure those are secure? There are plenty of HIPAA rules about what your practice can and cannot communicate via email, but, if you’re concerned about emails getting intercepted, I recommend using secure, encrypted email services such as Pretty Good Privacy (PGP). PGP is the technology Edward Snowden used to communicate with The Guardian reporters who helped him leak NSA information in 2013. It is an encryption system that is impossible to crack, and, while it may be overkill for communicating with patients, it is a useful way to encrypt sensitive communications among staff.
PGP relies on a technology called public-key cryptography to encrypt and secure emails. Think of it as a mailbox with two keys. One key is used to deposit mail in the mailbox. This is known as your public key, and you can give it out to anyone. Tweet it to the world, or post it on a billboard—it doesn’t matter. Anyone in possession of your public key will be able to send you encrypted email that only you can read. The other key is your private key. You—and only you—should have access to this private key or else anyone will be able to read your emails.
Secure file upload sites. If patients or business associates need to send you sensitive documents but don’t want to rely on PGP, consider using secure file upload sites, such as ShareFile (www.sharefile.com). These file sharing applications use bank-level encryption and security, so they are incredibly secure ways to share sensitive documents you wouldn’t want to fall into the wrong hands.
SECURITY CULTURE
It is worth mentioning that the most sophisticated tools in the world won’t help if you don’t actually use them. Your chance of getting struck by lightning is one in 960,000. According to the Ponemon Institute, the chances of your business experiencing a data breach are as high as one in four. What’s worse, the average cost of a data breach exceeds $3.5 million.2
In the WannaCry attack of 2017, global organizations like FedEx, Nissan, and the UK National Health Service were crippled by attacks that could have been prevented by simple security measures. It’s not that these organizations didn’t have the resources to combat such attacks; it was a lack of a security-minded culture that led to the cataclysmic results.
The first step in implementing a security practice is to create and foster a security-minded culture. It comes down to your people, your vendors, and the way you conduct business. Although I strongly recommend implementing some (or all) of the security tactics mentioned in this article, you must walk through the proper use of these tools with your staff. Helping employees and vendors understand why these tools are in use is the best way to ensure compliance and foster a security-minded culture.
Although the suggestions outlined in this article are certainly not an exhaustive list, their careful and successful implementation will place you well on your way to having a more secure ophthalmic practice and bringing you extra peace of mind.
Disclaimer: Messenger does not claim to be an expert on HIPAA compliance and cannot be held responsible for misuse of this information. Always consult a cybersecurity expert when installing or implementing cyber security measures.
1. Crowe J. 10 must-know cybersecurity statistics for 2018. https://blog.barkly.com/2018-cybersecurity-statistics. Accessed March 30, 2018.
2. Ponemon L. Know the odds: the cost of a data breach in 2017. https://securityintelligence.com/know-the-odds-the-cost-of-adata-breach-in-2017/. Accessed March 30, 2018.




